- S
-
Security Consulting
Our security consulting services help organizations systematically improve their information security. We identify risks, analyze vulnerabilities and develop practical security measures tailored to each organization.
Our support includes ISO 27001 projects, the development of security policies, awareness initiatives and guidance in IT and cloud projects. Our consulting is independent, clear and solution oriented.
We combine Swiss quality with technical expertise and support our clients on their path to sustainable and effective IT security.
- Price
- On request
- Hosting
- in Switzerland
- Company
- cyspro GmbH More about the provider

- #
-
"Dyna-Connect"
"Dyna-Connect" – Your Gateway to a Reliable Digital Workplace
A stable internet connection is the backbone of any modern IT environment. With "Dyna-Connect", we ensure that your business stays securely, reliably and efficiently connected – tailored to your specific requirements.
We identify the ideal internet solution for your needs and take care of the on-site configuration of all necessary components – including firewalls, switches and wireless access points.
Our service doesn’t stop after installation: we provide ongoing maintenance and support for all deployed components, ensuring everything continues to run smoothly – today and into the future.
As your needs evolve, we adapt the setup accordingly. This way, you benefit from a powerful, secure and future-proof connection – without the technical hassle.
- Price
- On request
- Hosting
- in Switzerland
- Company
- DynaNet GmbH More about the provider
- A
-
ANONAAS: Surf the internet without being detected or identified
ANONAAS has all the essentials to keep your browsing activity completely untraceable and anonymous on any network. Thanks to its military-grade encryption, zero-logging policy and a multi-hop network of international servers, ANONAAS is everything you need to surf the internet without being detected or identified.
- Price
- On request
- Technology
- ANONAAS is a worldwide, cross-continental multi-hop VPN solution, routing your Internet traffic through multiple servers (3+) in separate jurisdictions, ensuring anonymity, privacy, and data confidentiality. It protects your organisation against various threats such as network sniffing, tracking and surveillance without sacrificing the speed of your connection.
- Hosting
- in Switzerland
- Company
- Dreamlab Technologies AG More about the provider

- C
-
Cybersecurity
We take care of our customers' safety as our own
We offer innovative and high-performance, solutions to manage your security efficiently. As experts, we not only support you in setting up and using these solutions, but also in training your staff and helping you to adopt best practices.
We can guide you to:
• Implement security best practices
• manage compliance and governance
• audit your information systems
• Assess risks
• Detect threats and vulnerabilities
• Design remediation plans
• Respond to attacks
• And much more...
- Price
- On request
- Hosting
- in Switzerland
- Company
- Globaz SA More about the provider

-
CySOC: A 360-Degree View of your Cyber Dimension
CySOC’s comprehensive cyber SOC (security operations center) solution provides a holistic view into an organisation, offering a 360-degree view of the cyber dimension. Designed for critical infrastructure providers, private enterprises, and government entities, CySOC enables users to proactively detect, identify, analyse, and investigate anomalies within their IP-based infrastructures. By continuously monitoring network traffic and generating customisable dashboards, CySOC empowers organisations to defend against cybersecurity threats effectively. It strengthens their ability to monitor, prevent, detect, respond to, and manage cybersecurity incidents while providing valuable advice and support. With CySOC, users can enhance their cybersecurity efficiency, reduce personnel and incident resolution costs, and improve compliance with IT principles through streamlined reporting.
- Price
- On request
- Technology
- CySOC utilises advanced technology to improve security incident detection by constantly monitoring and analysing data activity. By continuously gathering and analysing real data like network packets and log files, CySOC accurately assesses the impact of potential threats and identifies the most suitable countermeasures. CySOC leverages optimisation and economies of scale to enhance its effectiveness and efficiency, not only saving valuable time and effort but also reducing costs.
- Hosting
- in Switzerland
- Company
- Dreamlab Technologies AG More about the provider

- H
-
HOPR network
HOPR keeps any exchange of data, private & secure.
If you use a Cloud service in Switzerland, HOPR can take care of your data to be up- & downloaded:
(1) with Authenticity (of sender & recipient)
(2) absolute Anonymity (external third parties cannot observe who does what & when)
(3) improved Reliability (decentralized communication protocol)
of all your data.
- Price
- On request
- Technology
- Blockchain Encryption
- Hosting
- available in Switzerland
- Company
- HOPR More about the provider

- I
-
IT solutions for all areas of IT
DIGITALIZATION
We support you in the conception, development and implementation of innovative technology solutions to successfully advance your company in digitalization.
MODERN WORKPLACE
Consulting, installation, service and operation for both cloud services and your local IT from a single source.
CYBER SECURITY
Fully comprehensive cyber security and data protection. We offer full cyber defense for your complete IT infrastructure.
BUSINESS APPLICATIONS
Optimal business software for more success. We work closely with you to develop your digitized IT system with the right applications for you.
CLOUD NATIVE DEVOPS
Deliver innovative applications faster. We accompany you in the transition to true cloud native solutions, operate your applications and provide you with full service.
CLOUD COMPUTING
Whether public, private, hybrid or multi-cloud, MTF supports your company in the transition to operating modern cloud platforms.
IT INFRASTRUCTURE
Whether on-premise, cloud or hybrid IT infrastructures, MTF, as one of the largest system houses in Switzerland, offers a full range of infrastructure services.
- Price
- On request
- Hosting
- in Switzerland
- Company
- MTF Solutions AG More about the provider

-
IT security services
The security products from Safe Swiss Cloud support information security managers in protecting against security breaches caused by ransomware and other types of malware. They help to continuously improve IT security and strengthen the defense against malware and ransomware.
The Safe Swiss Cloud security services offer a modular toolkit that can be used independently to improve the security of the IT infrastructure. These tools can be used both in the cloud and in the IT infrastructure on site.
Security monitoring: Receive early warnings and alerts about relevant security events in your IT environment.
- Price
- Siehe Webseite.
- Technology
- Multiple
- Hosting
- in Switzerland
- Company
- Safe Swiss Cloud AG More about the provider
- V
-
Virtual Server
A virtual server offers you performance and stability similar to a physical server, with additional high availability through our redundant platform.
You use your own server systems without having to worry about the procurement, operation and maintenance of server hardware. We provide you with a customized virtual server with full administrator access and any operating system.
With our high-performance server systems, our Enterprise SAN storage and SSD storage, we can adapt the virtual server exactly to your needs.
- Price
- from CHF 28.- / month
- Hosting
- in Switzerland
- Company
- SLYNET AG More about the provider
- S
-
Shared Storage
SharedStorage is our lean cloud storage solution for SMEs.
It enables shared central data management based on Nextcloud software. Shared storage offers the possibility to store and manage data, calendars and information centrally. At the same time, users remain independent of location with their work equipment. The data stocks between the individual users can be continuously synchronized and remain securely stored at all times in our data center in Switzerland.
The number of users is unlimited and they can be managed by you independently.
- Price
- from CHF 16.- / month
- Hosting
- in Switzerland
- Company
- SLYNET AG More about the provider
- N
-
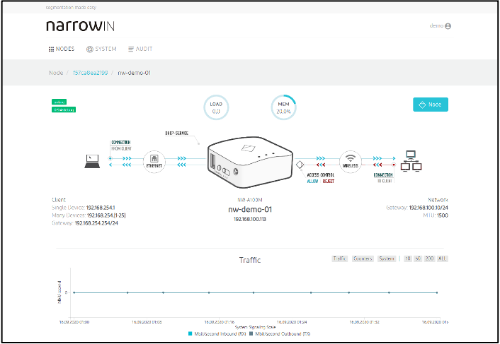
narrowin endpoint segmentation
Easy to hack, hard to patch: Protect vulnerable endpoints plug & play.
Our solution for micro-segmentation makes it possible to secure vulnerable devices and systems (e.g. legacy/unpatchable devices or devices without embedded security) with comparatively low costs and minimal effort. It offers direct protection against ransomware attacks. Typical use cases are medical devices, OT systems, research devices, Facility IoT etc.
- Price
- On request
- Hosting
- in Switzerland
- Company
- narrowin More about the provider
-
narrowin lightweight SDN
State-of-the-art network designs at minimal cost.
Our "lightweight SDN" approach offers the possibility to build secure and efficient networks without high costs and complexity. The proprietary platform for network management includes modern security concepts (zoning, NAC, etc.) out-of-the-box, as well as self-service features, automation and standard integrations. These advantages are combined with the unique price/performance ratio of Mikrotik hardware. The solution significantly simplifies network operation and relieves the strain on network and security personnel - without compromising on security and performance requirements.
- Price
- On request
- Hosting
- no data
- Company
- narrowin More about the provider
-
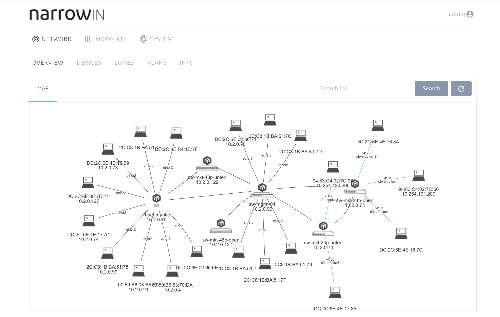
Network Segmentation
Analysis, design and implementation of a secure network architecture. Central design aspects are usually:
– Segmentation / zoning according to security levels
– Strong focus on endpoint security
– Use and build on the existing system landscape and tool chain
– Build automation & self-service to ensure efficient network operations
- Price
- On request
- Hosting
- no data
- Company
- narrowin More about the provider
- O
-
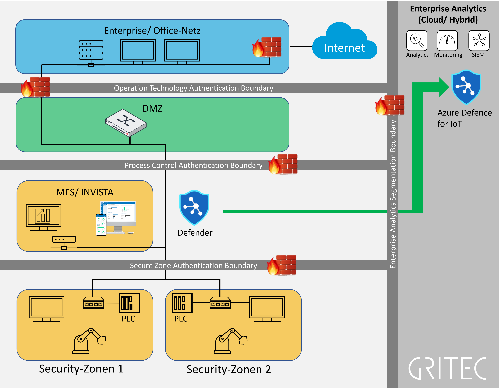
OT-Cyber Security IEC-62443
Digitization provides industrial companies with previously unimagined potential - but also confronts them with new challenges.
This also applies to cyber security. Gritec AG supports companies in making their production and products fit for cyber risks.
To do this, it relies on decades of industry expertise, existing standards (IEC-62443) and established strategies.
Services System Assess:
- System Testing/ Scanning
- OT-Infrastructure Check according to IEC 62443
- Consulting OT-Security IEC 62443
- Identification of technical vulnerabilities
Services Protect & Prevent:
- System architecture review
- Risk Assessment, Asset Values definition
- Assessment of processes and procedures
- Consulting for Security by Design
- Definition of effective measures
- Production network security (zoning, firewall, IDS, IPS, DPI)
- Price
- On request
- Technology
- Security IoT, Network Security, Security Consulting, Software for Engineering
- Hosting
- no data
- Company
- GRITEC AG More about the provider
- P
-
Penetration Testing
Cyber Attack Simulation
Through the use of proactive methods, we identify and target security vulnerabilities before they result in a malicious cybersecurity attack, preventing significant damage to your business.
Our comprehensive analysis identifies threat potentials, provides specific security recommendations, and ensures compliance with legal requirements to avoid reputational damage. Our security experts simulate realistic attacks on your systems, web applications, applications, IT infrastructures, mobile devices, IoT and OT, as well as cloud systems, to uncover weaknesses.
- Price
- On request
- Technology
- Blackbox-Tests, Whitebox-Tests, Greybox-Tests
- Hosting
- in Switzerland
- Company
- United Security Providers AG More about the provider

- S
-
SEC-CHECK®
Services for auditing IT-Infrastructure with the objective to improve the technical security settings in the existing environment.
- Price
- depending on project size
- Technology
- Proprietary
- Hosting
- no data
- Company
- SUA Telenet GmbH More about the provider

-
Secure Access as a Service
WAAP (Web Application + API Protection):
With Airlock Gateway, we offer a unique combination of protection mechanisms for business-critical, web-based applications and APIs. We thus fulfil the requirements of PCI DSS, ISAE 3000, ISO 27001 and FINMA RS 08/7, RS 08/21 and RS 18/3.
Airlock WAF systematically controls and filters all access at all levels before it reaches the customer application.
IAM - Identity & Access Management:
In combination with Airlock WAF, Airlock IAM enforces the upstream authentication and authorisation of users. This enables a secure, standardised and centralised single sign-on infrastructure.
We offer both WAF and IAM as a dedicated application or as a service.
As one of the few integrators at the Platinum level of the Airlock partner programme, aspectra meets the highest requirements in terms of know-how, industry and project experience and is able to implement and support even complex Airlock projects and installations.
- Price
- On request
- Technology
- Airlock Secure Access Hub
- Hosting
- in Switzerland
- Company
- aspectra AG More about the provider

-
Sedion Secure Box
The Sedion Secure Box is located in your company. It is up to you to define data that is particularly worthy of protection, which is then automatically freed from malware via Sedion Secure Box, encrypted and backed up externally as a replica in a former military bunker. In the event of a cyber attack, e.g. by a crypto-Trojan, the raw data can be quickly and purposefully restored. The Sedion Secure Box protects the company from expensive system failures and subsequent economic costs in the event of a cyber event.
- Price
- On request
- Hosting
- in Switzerland
- Company
- Sedion AG More about the provider

-
Swiss SafeLab M.ID Server
Many two-factor authentication solutions are based on additional devices/tokens. However, with these it is always cumbersome to carry them along. M. ID solves this problem in an elegant way: The OTP (one time password) is sent as text message to user's cell phone. Alternatively it can be generated with an app on smartphones or similar devices.
- Price
- On request
- Version
- 4.8.2 (10/7/2015)
- Technology
- Swiss SafeLab M.ID Server is a software security solution purely based on Java technology. Swiss SafeLab M.ID Server fits seamlessly in existing infrastructures as no additional hardware (Server, Appliances) have to be aquired.
- Hosting
- no data
- Company
- Swiss SafeLab GmbH More about the provider

- U
-
USP Network Authentication System®
The network access control (NAC) solution from United Security Providers blocks the path to malware and unauthorized access by screening all end devices that attempt to connect to a corporate network.
- Price
- On request
- Technology
- USP Network Authentication System®
- Hosting
- in Switzerland
- Company
- United Security Providers AG More about the provider
