- I
-
Individual software/hardware solution
GRITEC develops effective strategies and innovations to create sustainable added value for our customers.
With passion, our engineers and specialists meet complex challenges with knowledge, skill and innovation.
Our software architects develop concepts and define the best technologies.
Whatever you need - IoT fullstack solutions, Microsoft .NET Core, technologies, responsive designs with HTML and Javascript or Linux embedded solutions with Yocto Project - GRITEC is the right partner.
- Price
- On request
- Technology
- IoT, Azure, Web, Embedded-Solution, Industry 4.0, Smart Factory, Data Analytics, OT-Security, Desktop-Applikationen
- Hosting
- no data
- Company
- GRITEC AG More about the provider

- O
-
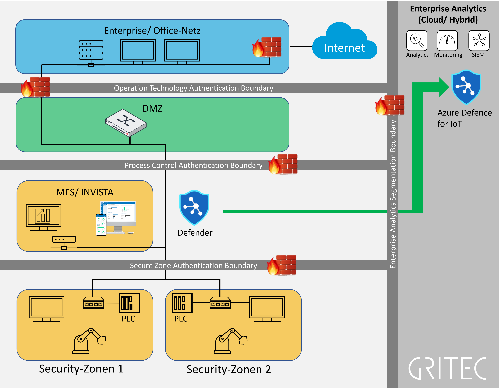
OT-Cyber Security IEC-62443
Digitization provides industrial companies with previously unimagined potential - but also confronts them with new challenges.
This also applies to cyber security. Gritec AG supports companies in making their production and products fit for cyber risks.
To do this, it relies on decades of industry expertise, existing standards (IEC-62443) and established strategies.
Services System Assess:
- System Testing/ Scanning
- OT-Infrastructure Check according to IEC 62443
- Consulting OT-Security IEC 62443
- Identification of technical vulnerabilities
Services Protect & Prevent:
- System architecture review
- Risk Assessment, Asset Values definition
- Assessment of processes and procedures
- Consulting for Security by Design
- Definition of effective measures
- Production network security (zoning, firewall, IDS, IPS, DPI)
- Price
- On request
- Technology
- Security IoT, Network Security, Security Consulting, Software for Engineering
- Hosting
- no data
- Company
- GRITEC AG More about the provider
- P
-
Penetration Testing
Cyber Attack Simulation
Through the use of proactive methods, we identify and target security vulnerabilities before they result in a malicious cybersecurity attack, preventing significant damage to your business.
Our comprehensive analysis identifies threat potentials, provides specific security recommendations, and ensures compliance with legal requirements to avoid reputational damage. Our security experts simulate realistic attacks on your systems, web applications, applications, IT infrastructures, mobile devices, IoT and OT, as well as cloud systems, to uncover weaknesses.
- Price
- On request
- Technology
- Blackbox-Tests, Whitebox-Tests, Greybox-Tests
- Hosting
- in Switzerland
- Company
- United Security Providers AG More about the provider

-
Product Development
With us you get tailored product development, professionally executed according to our processes, which also cover functional safety and cyber security.
Leave the tasks from specification & planning, implementation and testing to industrialization and production to us as your product development service provider. Since we take over the entire project management, your employees are freed up for other projects.
We can also take care of product maintenance for you. Since all intellectual property belongs to you at the end of the project, you can also take them over yourself, no lock-in...
- Price
- On request
- Technology
- C, C++, RTOS, Linux, Xamarin
- Hosting
- no data
- Company
- Solcept AG More about the provider
- T
-
ti&m Consulting and Software Development
Our industry expertise includes services in the AI, banking, insurance, public, transportation, e-government, retail and industry sectors.
Our vertically integrated offering ranges from consultation over software development, user experience design to solution hosting, allowing us to offer our clients unbeatable time-to-market combined with Swiss quality.
- Price
- On request
- Hosting
- available in Switzerland
- Company
- ti&m AG More about the provider