- S
-
Security Consulting
Our security consulting services help organizations systematically improve their information security. We identify risks, analyze vulnerabilities and develop practical security measures tailored to each organization.
Our support includes ISO 27001 projects, the development of security policies, awareness initiatives and guidance in IT and cloud projects. Our consulting is independent, clear and solution oriented.
We combine Swiss quality with technical expertise and support our clients on their path to sustainable and effective IT security.
- Price
- On request
- Hosting
- in Switzerland
- Company
- cyspro GmbH More about the provider

- C
-
Cybersecurity
We take care of our customers' safety as our own
We offer innovative and high-performance, solutions to manage your security efficiently. As experts, we not only support you in setting up and using these solutions, but also in training your staff and helping you to adopt best practices.
We can guide you to:
• Implement security best practices
• manage compliance and governance
• audit your information systems
• Assess risks
• Detect threats and vulnerabilities
• Design remediation plans
• Respond to attacks
• And much more...
- Price
- On request
- Hosting
- in Switzerland
- Company
- Globaz SA More about the provider

-
CyObs: High-Precision Cyber Radar System
CyObs is a groundbreaking high-precision cyber radar system that revolutionises the way nations and organizations perceive and safeguard their digital landscape. With unmatched accuracy and speed, CyObs empowers users to meticulously measure, visualise, and analyse the vast realm of cyberspace. By providing a comprehensive understanding of their digital infrastructure, CyObs enables organisations to reduce their attack surface and fortify the security of their online assets. Undeniably, CyObs stands as the cornerstone of any robust national cyber defense strategy.
- Price
- On request
- Technology
- CyObs utilises state-of-the-art technology to offer comprehensive protection against malicious attacks. By employing proactive threat identification, advanced analytics, and a systematic approach to risk mitigation, CyObs ensures comprehensive security. Powered by cutting-edge algorithms and advanced data processing, CyObs provides unparalleled accuracy and clarity in assessing and comprehending the cyberspace. Its exceptional precision, speed, and visualisation capabilities make it a valuable tool for implementing proactive cyber defense strategies in an ever-changing digital landscape.
- Hosting
- in Switzerland
- Company
- Dreamlab Technologies AG More about the provider

- F
-
FraudGuardian
FraudGuardian enables financial institutions to address fraud challenges (e.g. mobile banking, payment fraud, e-banking, account takeover, identity theft) with out-of-the-box controls packaged in bundles. These controls ensure continuous auditing of human behavior across channels, IT layers and financial transactions.
FraudGuardian is backed by NG|Screener, an innovative enterprise software platform that uses Big Data technology, predictive analytics, and user behavior analytics to combine and standardize data from across the entire banking system. FraudGuardian prevents fraud before it happens. Its real-time auditing interface allows you to easily view all detected activities anytime.
- Price
- On request
- Version
- 6.0
- Technology
- Big Data
- Hosting
- no data
- Company
- NetGuardians More about the provider
- E
-
ELCA Advisory
ELCA’s consulting team includes more than 35 experienced consultants, who advise organizations in every sector on implementing their business strategies and reaching their objectives efficiently with the help of the most up-to-date technologies. We define future-proof, coherent IT strategies and business architectures and implement them sustainably in the organization. Our core competencies include strategic IT consulting, digital transformation, business and operational process analysis, business architecture, requirements engineering, change management, programm and project management as well as user experience, quality assurance and test management.
- Price
- On request
- Technology
- Own and partner technologies: https://www.elca.ch/en/partners
- Hosting
- in Switzerland
- Company
- ELCA Informatik AG More about the provider

- N
-
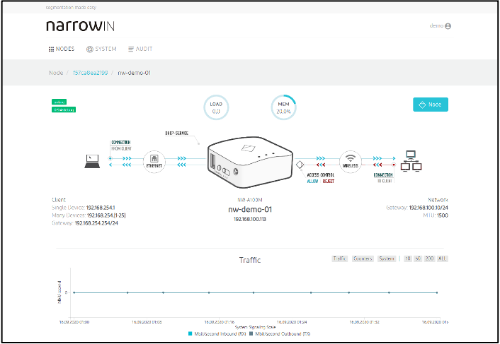
narrowin endpoint segmentation
Easy to hack, hard to patch: Protect vulnerable endpoints plug & play.
Our solution for micro-segmentation makes it possible to secure vulnerable devices and systems (e.g. legacy/unpatchable devices or devices without embedded security) with comparatively low costs and minimal effort. It offers direct protection against ransomware attacks. Typical use cases are medical devices, OT systems, research devices, Facility IoT etc.
- Price
- On request
- Hosting
- in Switzerland
- Company
- narrowin More about the provider
-
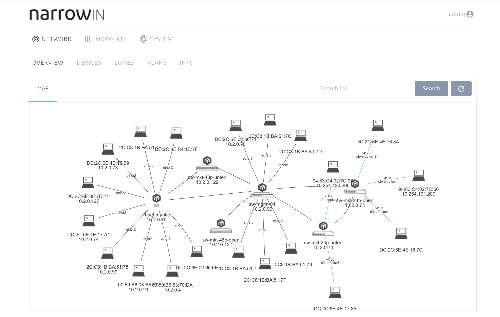
narrowin lightweight SDN
State-of-the-art network designs at minimal cost.
Our "lightweight SDN" approach offers the possibility to build secure and efficient networks without high costs and complexity. The proprietary platform for network management includes modern security concepts (zoning, NAC, etc.) out-of-the-box, as well as self-service features, automation and standard integrations. These advantages are combined with the unique price/performance ratio of Mikrotik hardware. The solution significantly simplifies network operation and relieves the strain on network and security personnel - without compromising on security and performance requirements.
- Price
- On request
- Hosting
- no data
- Company
- narrowin More about the provider
-
Network Segmentation
Analysis, design and implementation of a secure network architecture. Central design aspects are usually:
– Segmentation / zoning according to security levels
– Strong focus on endpoint security
– Use and build on the existing system landscape and tool chain
– Build automation & self-service to ensure efficient network operations
- Price
- On request
- Hosting
- no data
- Company
- narrowin More about the provider
- P
-
Penetration Testing
Cyber Attack Simulation
Through the use of proactive methods, we identify and target security vulnerabilities before they result in a malicious cybersecurity attack, preventing significant damage to your business.
Our comprehensive analysis identifies threat potentials, provides specific security recommendations, and ensures compliance with legal requirements to avoid reputational damage. Our security experts simulate realistic attacks on your systems, web applications, applications, IT infrastructures, mobile devices, IoT and OT, as well as cloud systems, to uncover weaknesses.
- Price
- On request
- Technology
- Blackbox-Tests, Whitebox-Tests, Greybox-Tests
- Hosting
- in Switzerland
- Company
- United Security Providers AG More about the provider

-
Penetration Tests
What is the best way to test the security of your IT infrastructure, systems and organization? Exactly, with a hacker attack!
During a penetration test, our Cyber Seurity experts perform a real attack. This shows whether the infrastructure is sufficiently protected against attacks from outside and inside and whether it is in line with the accepted residual risks. Our approach is based on the recognized methods OWASP, OSSTMM and ISO 27001.
- Price
- On request
- Hosting
- no data
- Company
- Brielmayer Consulting GmbH More about the provider
- R
-
Robust IT Security Assessment
Safeguard your organization's and customers' sensitive data with our thorough IT security assessment. Our security experts will evaluate your overall IT infrastructure, including your customer portals, to identify vulnerabilities and provide actionable recommendations. Trust us to fortify your cybersecurity and maintain your business's resilience.
- Price
- On request
- Hosting
- in Switzerland
- Company
- Luzid.Tech GmbH More about the provider
- S
-
SEC-CHECK®
Software for auditing IT-Infrastructure with the objective to improve the technical security settings in the existing environment.
- Price
- SME from CHF 480
- Technology
- Proprietary
- Hosting
- no data
- Company
- SUA Telenet GmbH More about the provider

-
SEC-CHECK®
Services for auditing IT-Infrastructure with the objective to improve the technical security settings in the existing environment.
- Price
- depending on project size
- Technology
- Proprietary
- Hosting
- no data
- Company
- SUA Telenet GmbH More about the provider

-
Security Consulting
Ergonomics, a leading Consulting Company in areas of Integrated Security, can support you in recognizing and resolving enterprise wide IT risks, dangers, and weak spots. Over the years, Ergonomics Security Consultants have gained immense knowhow – valuable in tackling the most challenging Organisational and Technical IT Security issues.
On a daily basis, we deal with issues surrounding Secure IT Systems and Networks, Information Security Management, Data Protection, Crisis Management, Social Engineering, Security Concepts, and Security Audits. Our Consultants have a plethora of skills covering technical and business areas, and are therefore able to support you in defining your strategy and implementing it to a future state, or being your professional coach in close collaboration with you.
International Credit Card organisations issue stringent security requirements to their contractual partners based on PCI Data Security Standard. Our Certified Security Auditors/Certified Security Assessors accompany you from analysis right up to implementation, and ensure that the highest security standards can be satisfied.
- Price
- On request
- Technology
- Compliance (ISO 27001, PCI DSS), Schwachstellenanalysen, SCADA Security
- Hosting
- no data
- Company
- Ergonomics AG More about the provider
- T
-
TopSec
In Short:
- Web UI for automated avaloq authorization assignment process (Oracle APEX)
- Workflow and order-based
- Minimum effort, maximum security, full transparency
- FINMA-compliant thanks to closed security and compliance with the “least privilege” principle
TopSec provides you with technical support that largely automates your Avaloq authorization assignment process for functional roles and eliminates the risk of faulty deployments. Whether for the development of a release on the test environment or as a hotfix in production - scripts are created, verified and synchronized over all selected databases in just a few seconds. By complying with the “least privilege” principle required by FINMA as well as the complete transparency and traceability of each individual process step, time-consuming analyses and reports are a thing of the past. Audit-compliant documentation of all authorization assignments is already integrated in the tool.
- Price
- On request
- Technology
- Oracle Apex, Avaloq, PLSQL
- Hosting
- in Switzerland
- Company
- Asubium More about the provider
